Newsletter 17 — MythX, False Positives on chain, & Front Running
Sign up to get this newsletter in your inbox every week: https://tinyletter.com/smart-contract-security/
Happy Sunday everyone! I normally try to have this out by Saturday night, so I’m a bit tardy this week.
Brief housekeeping note: in the last couple weeks my emails have started getting caught by a lot of spam filters. If you find this in your spam, and your email client gives you an explanation for why, please let me know! I’ve gone back to the previous subject format (ie. ===), so… maybe that will help?
Lastly, I’m experimenting a bit with how I include links. TinyLetter masks them with lame tracking URLs, and it’s annoying to have no idea where a link will take you. If you think this approach is better, or if it impacts the readability, I’d appreciate a quick note from you.
Distilled News
Why you should Buidl on the MythX API
(medium.com/consensys-diligence)
I’m so excited that our MythX platform will go into public beta in early March! By combining static code analysis, guided grey-box fuzzing and symbolic execution it covers twice as many security weaknesses as Mythril Classic, and is 10 times faster.
Tool devs who integrate can earn 25% on subscription revenues generated by their users.
Academic paper: Smart contract vulns does anyone care?
You may recall several papers in the last year or so, each introducing a new analysis technique or tool, and listing some very large number of vulnerable on-chain contracts they had identified.
This paper surveys those findings, and suggests that there were quite a few false positives in the findings.
We find that at most 504 out of 21,270 contracts have been subjected to exploits. This corresponds to at most 9,094 ETH (1 million USD1), or only 0.30% of the 3 million ETH (350 million USD) claimed in some of the papers. While we are certainly not implying that smart contract vulnerability research is without merit, our results suggest that the potential impact of vulnerable code had been greatly exaggerated.
Interestingly, they also found surprisingly little overlap in the set of broken contracts each paper listed, which further suggests a large number of false positives.
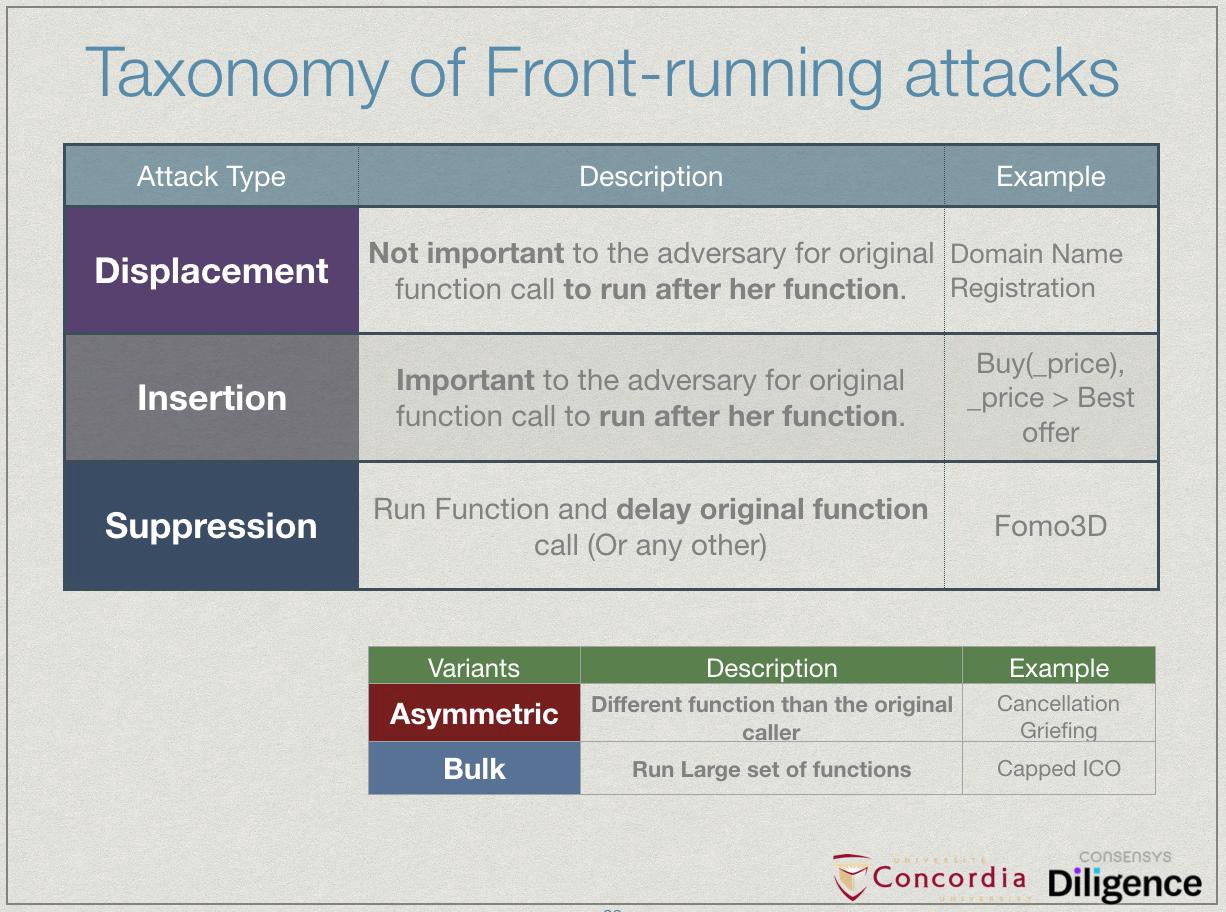
Taxonomy of Front Running Attacks
(post medium.com/consensys-diligence, pdf at https://arxiv.org/abs/1902.05164)
“Front Running” attacks on smart contracts occur anytime an attacker can gain an advantage by inserting a transaction before yours. As Phil Daian has described in detail (ie. his Devcon4 talk), this is very common with decentralized exchanges (ie. seeing a large price-moving buy-order, and racing to get a buy-order in first). However, there are several variations on this pattern, which are different enough to makes the whole concept of “front running” feel vague.
At last week’s Financial Cryptography conference, my teammate Shayan Eskandari presented a paper which adds a lot of clarity, by describing 3 distinct categories of front running (‘Displacement’, ‘Insertion’ and ‘Suppression’). This slide sums it up nicely:
Links
-
Last call on EIP 615: Subroutines and static jumps for the EVM (ethereum-magicians forum).
-
Can the capabilities of
CREATEbe stretched enough to fulfill the intent ofCREATE2? Not quite, but if you ignore the snarky tone, it’s a good thought experiment. (“Why CREATE2” on Medium). -
Eveem creator Tomasz Kolinko, has some nice slides about: “Finding all the underflows in mainnet contracts” (PDF at eveem.org).
-
Coinbase CEO Brian Armstrong’s twitter thread suggesting that QuadrigaCX has been running “fractionally” (a la MtGOX), ever since June 2017 (reddit post) when they locked 67000 ETH in an ETH/ETC splitter contract (Etherscan).
-
From Zac Mitton, a “generalized merkle-patricia-proof module” in js that now supports Ethereum state proofs (github.com/zmitton).
Want to help make this newsletter better? Join the #maurelians-newsletter channel in MythX’s discord chat.
Want more weekly goodness? Read my friends’ stuff!
- Ben’s “What’s new in ETH 2.0”
- Evan’s “Week in Ethereum”
This newsletter is supported by ConsenSys Diligence, where I work. We can help with all things smart contract security; auditing, secure development guidance, and training.
We’re also building the MythX platform for smart contract security analysis.
We’re hiring!
Developer — Security Analysis Tools Frontend and Dapp Engineer, MythX Marketing and Brand Manager, MythX Security Engineer and Auditor — Smart Contracts Senior Technical Recruiter Smart Contract Security Business Development Lead Technical Product Manager, MythX
Thinking about smart contract security? We can provide training, ongoing advice, and smart contract auditing. Contact us.