AraGraph - DAO Permissions Visualized
Aragon based Decentralized Autonomous Organizations (DAOs) can easily get complex to understand. The DAO, its managers, and the permissions for each application are intertwined and there are many ways of getting it wrong.
Introducing AraGraph — a simple tool the team at ConsenSys Diligence recently contributed to the Aragon community that visualizes DAO application and permission specifications.
AraGraph
The cool thing about working with a world-class team of security enthusiasts here at ConsenSys Diligence is that we get to work with super-smart and innovative individuals, buidling solutions that shape our future world.
One of our missions at Diligence is to do our part in helping communities and the ecosystem to level-up, not only by providing auditing services but by helping communities to embed security by default.
Over the years we have performed a series of audits for our innovative friends at Aragon who are building a smart contract system, ecosystem and a community that aims to empower people to freely organize and collaborate in Decentralized Autonomous Organizations.
As part of this work, we audited the Aragon DAO Templates, formerly known as DAO-Kits. These templates are smart contracts that deploy a new DAO and its applications configured for a specific scenario. They are the construction plan for your decentralized organization and therefore critical to the security of your organization.
The DAO Templates repository currently lists the following default templates:
- Bare
- Membership
- Reputation
- Company
- Company-Board
- Trust
A description of the different DAO templates can be found in the Aragon DAO Templates Repository or in the Audit Report.
Visualizing DAOs
You may deploy your own template contract that creates specific DAO scenarios or you might want to reuse the templates contracts provided by the Aragon Foundation. Either way you have to trust that whatever is being set up is working according to the trust model described in the DAO template specification.
DAO templates specifications come in a variety of flavors:
- human readable documentation
- machine readable YAML (see Aragon DAO Templates Descriptor), or
- source code
Many things can go wrong, including coding mistakes, specification errors and permission loopholes.
For instance, templates may choose to remain in control of parts of the DAO even after the deployment or the DAO application permissions setup is inconsistent and allows some stakeholders or outsiders to perform privileged actions or potentially drain funds without the DAO stakeholders consent.
Until now there was no easy way to visually review the DAO permission setup. AraGraph aims to fill that gap by allowing designers, auditors, and users to verify and cross-check the trust model for a DAO.
Check out the DAO Templates Audit Report to see AraGraph in action on a real audit. It is also a good starting point to learn more about Aragon DAOs from a security perspective!
How does it work?
It is as easy as installing AraGraph command-line utility via npm install -g aragraph. Then execute $ aragraph <dao.yaml|Readme.md> with either
- the path to the YAML specification of the DAO, or
- the path to the Markdown Table containing a specification of the DAO
Rendering DAO Permissions with AraGraph and VSCode
In the example above, we call AraGraph from within a Visual Studio Code instance and use the VSCode Plantuml extension to render the newly generated dao.plantuml. This visualization can even be enriched with templated security information for the individual DAO components — but that is something we’ll leave for another blog post :)
Alright, it is really that easy. You get a visual representation of the DAO permission setup - optionally enriched with templated security information - to get a better understanding about your DAO.
Example
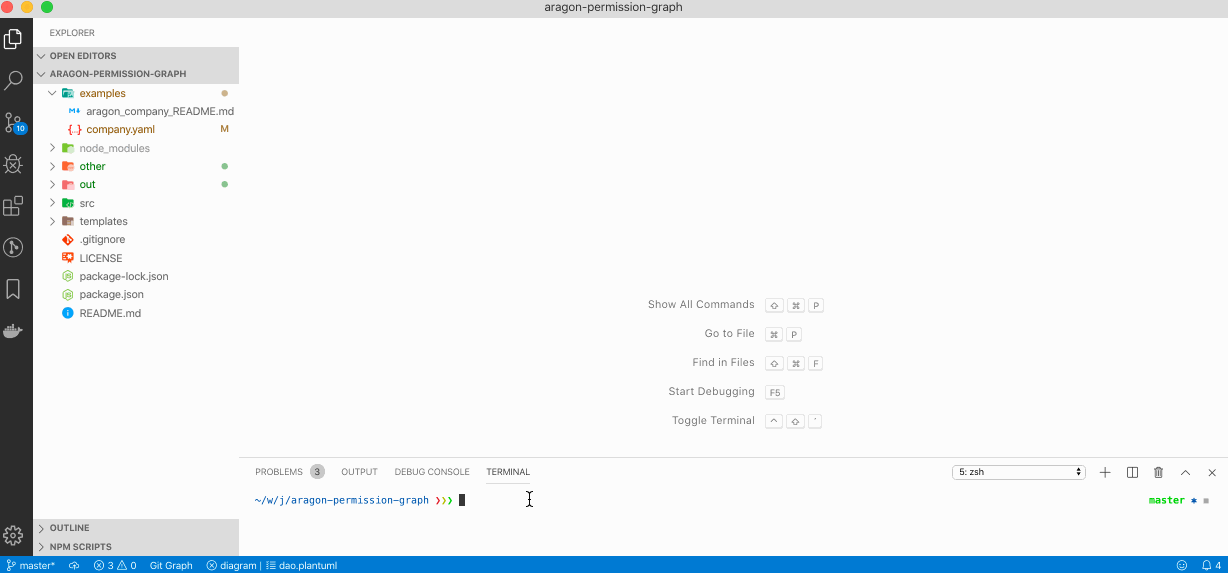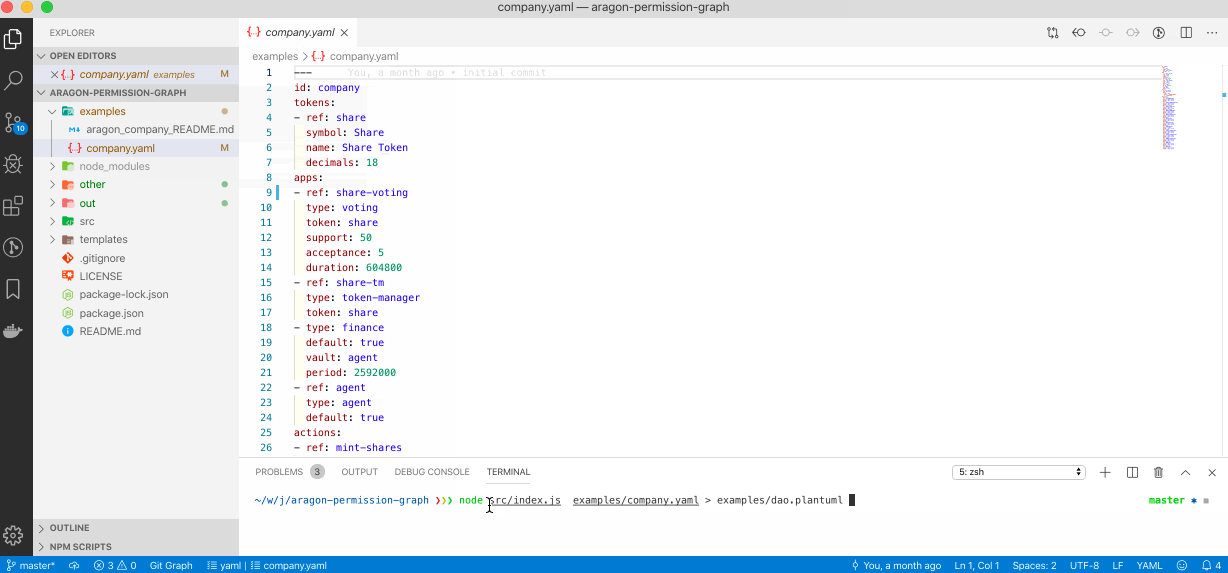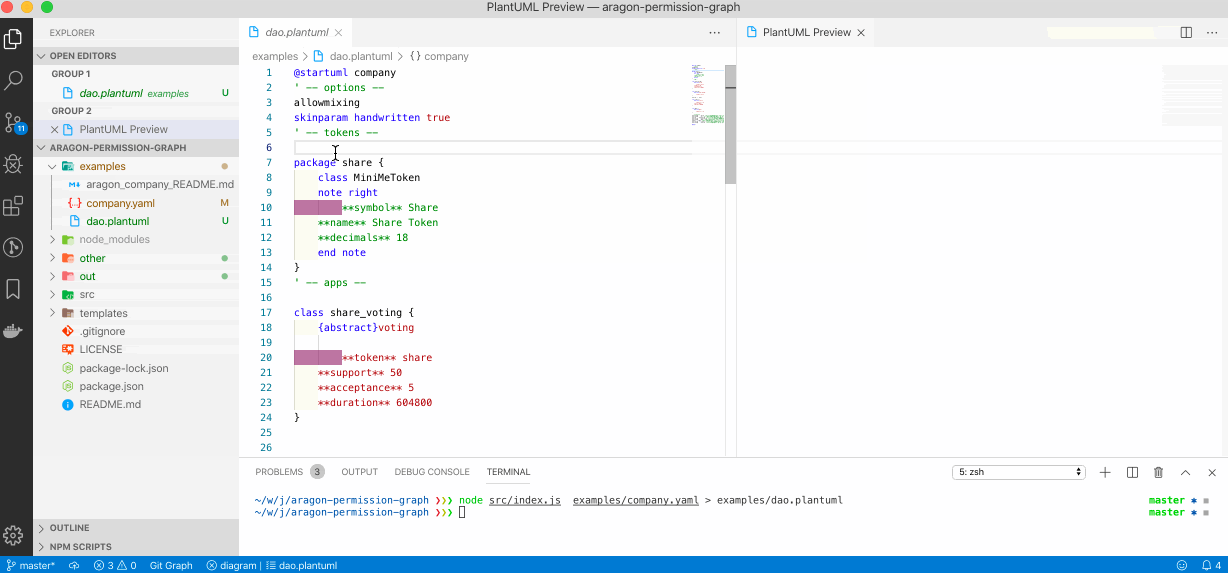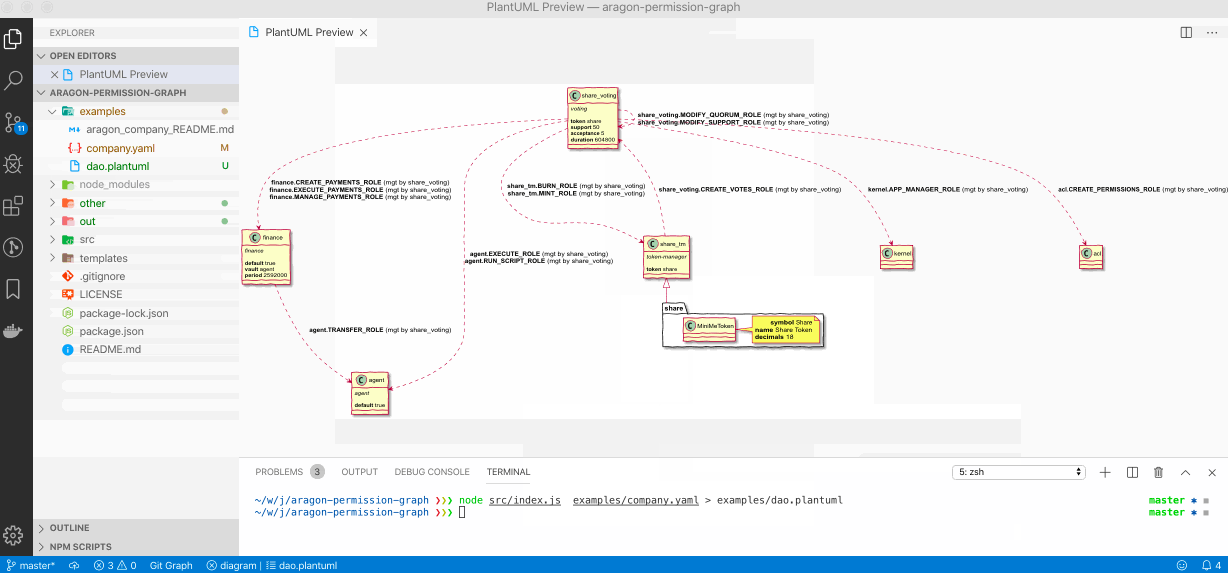
DAO Example
Every component that comprises the DAO is visualized in the output graph (yellow boxes). When available, the component will be annotated with its configuration (usually only when generated from yaml). Relations describe the permission setup.
For instance, in the DAO depicted above one can see that share_voting rules the DAO. All the permissions are managed by the Shareholder Voting Application. Only Shareholders can vote for modification of Quorum and Support of the Voting Application. They also rule the Kernel and can create new permissions via ACL. Votings can only be created by Token holders of the token that is managed by the TokenManager (share_tm) because the Token Manager has permissions to create votes on the Voting Application. The Share Token governs the DAO and any token holder can create a Voting by calling out to the Voting Application via the TokenManager (share_tm).
Security
The tool supports your internal efforts when reviewing the DAO design. While it allows you to find inconsistencies early, a thorough security audit is still highly recommended.
Generating a visual representation of a DAO specification does not verify that the DAOs code actually deploys what is specified in the documentation, nor does it check if the specification is consistent with the DAO applications capabilities and intended way of using them. Loopholes in the design and coding flaws can have severe impact on the organization.
A visual representation of the organization helps with understanding the DAOs anatomy more quickly and gives you the tool to challenge the design from a different perspective. It is therefore a perfect addition to your arsenal of tools supporting security activities in your Secure Development Lifecycle.
That said, the security community is always happy to consult with you on any security related questions. Get in touch with us now.
Future Potential
Visualization is key to reducing complexity and we believe that providing the Aragon community with tools that help them create secure-by-default applications and projects will allow us all to advance in this space.
One idea we are experimenting with is to enrich visualizations with security annotations for DAO applications. This is still in an early phase but can further reduce the risk overseeing design flaws in the internal review process.
Furthermore, we believe that a similar visualization should be part of the Aragon UX for deploying DAOs, reducing ambiguities and pushing for even more transparency.
Thinking about smart contract security? We can provide training, ongoing advice, and smart contract auditing. Contact us.